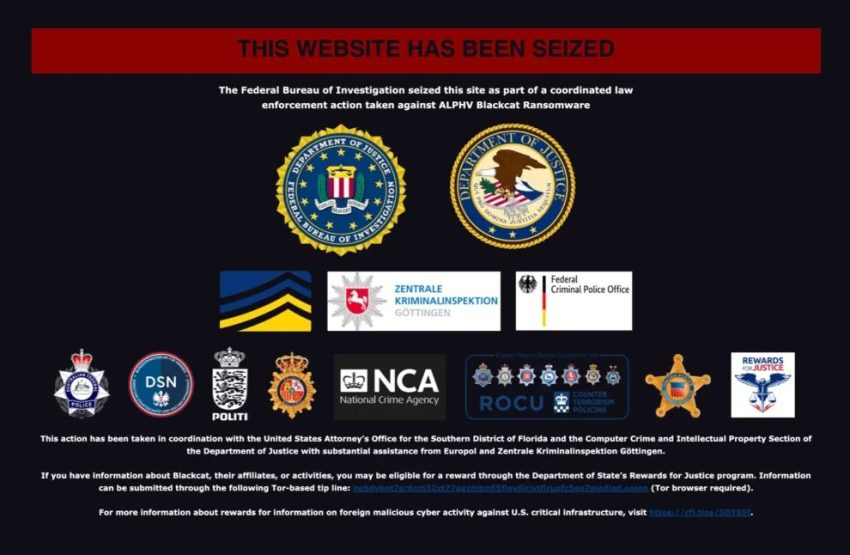
On Tuesday, December 19, 2023, the Department of Justice announced the disruption of a notorious Russian ransomware group’s dark website. The announcement came shortly after the ransomware group’s dark web presence was overruled with a seizure notice.
ALPHV/ Blackcat, a Russian ransomware group, Darknet Forum and Market were seized as part of an internationally coordinated law enforcement action against the group. The ransomware group is believed to be the successor of the “REvil” hacking group.
Key Takeaways
- The US Department of Justice disrupted the notorious ALPHV/BlackCat ransomware group’s dark website.
- BlackCat is a prolific Darknet ransomware group that has targeted critical infrastructure in the US and amassed millions in ransom.
- Law enforcement gained access to BlackCat’s network and seized its dark web assets, including victim communication sites and data leak sites.
- The FBI developed a decryption tool that allowed over 500 victims to restore their systems.
- BlackCat claims to have unseized its main dark website, but both the FBI and BlackCat have a private key for the .onion address. Laughing off the attack
Blackcat has comprised networks of more than 1,000 victims to amass hundreds of millions of US dollars. The group claims to have compromised several prolific sites, such as Reddit, the U.K.’s Barts Health NHS Trust, and healthcare company Norton.
The Department of Justice alleges the ransomware group specifically targets critical infrastructure in the United States, such as government facilities, emergency services, defence industrial base companies, critical manufacturing, healthcare and public health facilities, as well as schools.
Blackcat uses a ransomware-as-a-service model, where the developers of the group create and update ransomware to maintain the illicit internet infrastructure. Affiliates of the group are responsible for scouting and attacking high-profile institutions with ransomware.
Affiliates of the ransomware group have gained initial access to the victim’s networks using several methods, including “leveraging compromised user credentials to gain initial access to the victim system,” according to the DOJ.
Once Blackcat actors gain access, an affiliate will steal sensitive data and encrypt the victim’s network. The group uses extortion tactics as a model of attack and seeks ransom in exchange for decrypting the victim’s network.
When the demanded ransom is not paid over to the group, the victim’s information is leaked across the dark web. Exposing the victim’s sensitive information and making them susceptible to cyber-attacks.
In November, the ALPHV resorted to extreme measures and filed a complaint with the U.S. Securities and Exchange Commission (SEC). The complaint alleged that MeridianLink failed to disclose “a significant breach compromising customer data and operational information.”
What We Know About The Investigation
Over the past 18 months, the ALPHV ransomware group emerged as the second most prolific threat, claiming millions of dollars in ransom. The global scale of the group’s crimes led to multiple law enforcement agencies conducting a combined investigation.
The U.S. Department of Justice said in an announcement that an international operation led by the FBI, enabled U.S. authorities to gain information into the ransomware group’s computer to seize “several websites” that the group operated.
A Blackcat search warrant revealed that the FBI allegedly engaged with a “confidential human source” close to the ransomware gang. The source provided field agents with credentials to access ALPHV/BlackCat’s affiliate panel used to manage the gang’s victims. The Department of Justice previously appealed to anyone offering a reward for information with regards to Blackcat ransomware, its affiliates or its activities.
During the encryption process, the victim receives a ransom note
containing a unique Tor .onion address through which to communicate with the
Blackcat Ransomware Group (a “victim communication site”). The ransom note also
references a primary “leak” site Tor address through which the Blackcat Ransomware
Group discloses information about victims and the data they have stolen. This primary
leak site consists of the main Tor address given to victims and multiple other Tor
addresses that facilitate this main address’s operationThe Warrent Claims
Earlier this month, the group’s dark website briefly went offline. The reasons for the outage were unknown. However, it’s alleged that law enforcement agencies had temporarily managed to derail the group’s activities.
In an application for a search warrant, US authorities state that they “gained visibility into the Blackcat Ransomware Group’s network” and further data on its dark-web assets. The FBI said they accessed 946 public-private key pairs for Tor-hidden sites.
The Blackcat gang used these Tor-hidden sites to communicate with victims and host the group’s blog. Law enforcement agents also managed to reveal sites used to host leaked data and the control panels affiliates used to set up malware infections.
The FBI also developed a decryption tool that allowed field offices across the U.S. and law enforcement partners from around the globe to offer over 500 affected victims the capability to restore their systems.
As a result of our office’s tireless efforts, alongside FBI Miami, U.S. Secret Service, and our foreign law enforcement partners, we have provided Blackcat’s victims, in the Southern District of Florida and around the world, the opportunity to get back on their feet and to fortify their digital defenses. We will continue to focus on holding the people behind the Blackcat ransomware group accountable for their crimes.
U.S. Attorney Markenzy Lapointe for the Southern District of Florida said in a statement
In disrupting the BlackCat ransomware group, the Justice Department has once again hacked the hackers. With a decryption tool provided by the FBI to hundreds of ransomware victims worldwide, businesses and schools were able to reopen, and healthcare and emergency services were able to come back online.”
U.S. Deputy Attorney General Lisa Monaco
An attached affidavit in an application for a search warrant revealed that the FBI worked with hundreds (400) of victims in the United States and internationally to implement its decryption tool. The decryption tool saved multiple victims from ransom demands totaling an estimated $68 million.
U.S Deputy Attorney General Lisa Monaco further committed to continuing to prioritize the disruption and to “place victims at the center of our strategy to dismantle the ecosystem fueling cybercrime.” The international takedown of Blackcat’s dark website involved law enforcement agencies from the United Kingdom, Denmark, Germany, Spain, and Australia.
BlackCat Laughs off Siezed Website
In reaction to the FBI’s claimed seizure of Blackcat’s darknet Forum, the group claimed it had unseized its main dark website. The ransomware group discredited the FBI’s claim by pointing it to a web server the miscreant control.
The ransomware group continued to use its unseized, Darknet site to name a new alleged victim of its ransomware. However, both the FBI and Blackcat have a private key for the .onion address of the dark website.
The initial seizure of the group’s dark web blog on December 7, followed by a two-day downtime period, was unusual for a ransomware gang’s blog. The reappearance of the without a list of previous victims indicates that law enforcement agents had successfully seized the dark web blog earlier in the month.
Other ransomware groups have pointed out Blackcat’s lack of explanation for the downtime to the successful takedown of a law enforcement operation.