NOTE: LOCKBIT HAS SINCE RETURNED SEE OUR ARTICLE COVERING THEIR RETURN
International law enforcement agencies, including the U.S. Federal Bureau of Investigation and the U.K. National Crime Agency, have seized a dark website operated by the LockBit ransomware gang. The U.S. Department of Justice announced the disruption of LockBit, one of the world’s most prolific ransomware groups, which has targeted over 2,000 victims and netted more than $120 million in ransom payments. The operation involved seizing the gang’s infrastructure and indicting two Russian nationals for their involvement in deploying LockBit ransomware.
Key Insights
- Operation Chronos involved the U.S. Department of Justice, the U.K. National Crime Agency, and the FBI worked together to seize and capture those running LockBit.
- LockBit is known for targeting over 2,000 victims and obtaining over $120 million in ransom payments.
- The group operates on a “ransomware-as-a-service” model, recruiting affiliates to deploy ransomware.
- High-profile victims of LockBit include TSMC, Boeing, UK’s Royal Mail, and Fulton County, Georgia.
- In 2023, LockBit was responsible for about 22% of all ransomware victims, with over a thousand cases recorded by NCC Group.
- A notice on LockBit’s leak site announced it was under the control of the National Crime Agency and international law enforcement.
- Law enforcement seized 34 servers and over 200 cryptocurrency wallets linked to LockBit.
- Decryption keys obtained during the operation will aid victims in regaining access to their data.
A collaboration of international law enforcement agencies, including the U.K. National Crime Agency and U.S. Federal Bureau of Investigation, have seized a dark website belonging to the LockBit ransomware gang.
The US Department of Justice joined other international agencies today and announced the disruption of the LockBit ransomware group’s dark website. LockBit is currently one of the most prolific ransomware groups in the world and has targeted over 2,000 victims, netting over $120 million in ransomware payments.
The US Department of Justice confirmed that the ransomware group accesses victims’ information with a LockBit variant. Like other ransomware variants, it operates in the “ransomware-as-a-service” (RaaS) model.
Developers of the software recruit affiliates to deploy the ransomware and maintain a control panel to provide the affiliates with the appropriate mechanism to deploy the LockBit ransomware.
Affiliates of the group are then responsible for identifying and unlawfully infiltrating vulnerable computer networks with the help of stolen access credentials or through hacking the network. LockBit ransomware is then deployed in the system allowing the developers to encrypt and steal data.
In 2023, the ransomware group claimed responsibility for exploiting some of the world’s largest corporations including chipmaker TSMC, aerospace giant Boeing, UK’s Royal Mail, Industrial and Commercial Bank of China, and Fulton County, Georgia.
Matt Hull, head of threat Intelligence at cybersecurity NCC Group, said that more than a thousand victims of LockBit were recorded by the company in 2023. This amounts to approximately 22% of all ransomware victims in 2023.
Hattie Hafenrichter, a spokesperson for the U.K.’s National Crime Agency, announced that “LockBit services have been disrupted as a result of international law enforcement action.” A notice message on LockBit’s leak site confirmed that the site is “now under the control of the National Crime Agency of the U.K., working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos’.”
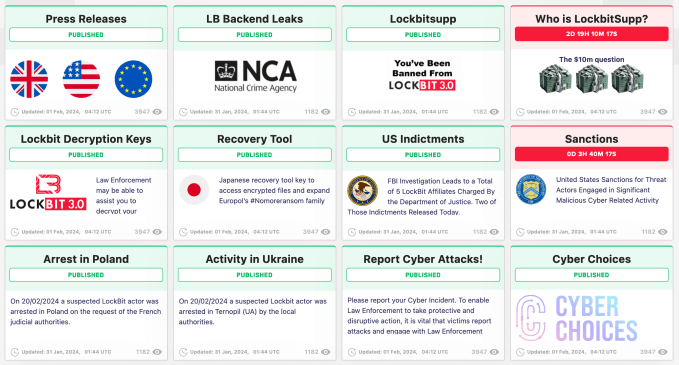
LockBit’s leak site now hosts information that exposes LockBit’s operations. The information includes leaks and details of the ransomware group’s leader, known as LockBitSupp.
What We Know About the Incident
Operation Chronos headed by the NCA and coordinated by Europol was tasked with bringing down LockBit’s criminal operation. The operation also included other international police organizations from Australia, Canada, France, Finland, Germany, the Netherlands, Japan, Sweden, Switzerland, and the United States.
On Monday, February 19, Europol confirmed that the operation “resulted in the compromise of LockBit’s primary platform and other critical infrastructure that enabled their criminal enterprise.”
The takedown included 34 servers across Europe, the United Kingdom, and the United States. Law enforcement seized over 200 cryptocurrency wallets, of which the value remains undisclosed.
Operation Cronos’s task force members allege to have obtained decryption keys from LockBit’s seized infrastructure. The decryption keys will help victims of the ransomware gang to regain access to their data.
In a separate incident, the U.S. Justice Department unsealed an indictment order against Artur Sungatov and Ivan Gennadievich Kondratyev for their alleged part in deploying LockBit cyberattacks throughout the United States.
According to the indictment order, Sungatov allegedly infiltrated LockBit’s ransomware against large corporations and funded additional LockBit attacks against other corporations in January 2021.
Kondratyev allegedly deployed LockBit ransomware against multiple victims. His indictment order alleges that he operated under the alias “Bassterlord” and deployed LockBit ransomware against municipal and private targets in Puerto Rico, New York, and Oregon.
Kondratyev’s indictment order obtained in the Northern District of California also charges him with three criminal counts. The charges arise from his use of the Sodinokibi ransomware variant to “encrypt data, exfiltrate victim information, and extort a ransom payment from a corporate victim based in Alameda County, California.”
Sungatov and Kondratyev allegedly partnered and conspired with the LockBit ransomware gang. Other members who joined included Russian nationals Mikhail Pavlovich Matveev and Mikhail Vasiliev.
Arrests and Indictment Orders
U.S. Attorney Philip R. Sellinger for the District of New Jersey said “Today’s indictment, unsealed as part of a global coordinated action against the most active ransomware group in the world, brings to five the total number of LockBit members charged by my office and our FBI and Computer Crime and Intellectual Property Section partners for their crimes.”
In November 2022, a criminal complaint was filed in the District of New Jersey. The complaint charged Mikhail Vasiliev with his involvement in the LockBit ransomware syndicate. Vasiliev is currently detained in Canada and awaiting extradition to the United States.
In May 2023, two indictment orders in Washington, D.C. charged Mikhail Pavlovich Matveev with deploying LockBit ransomware to attack several victims throughout the United States. One of the victims was the Washington, D.C. Metropolitan Police Department.
Matveev is believed to live in the Russian enclave of Kaliningrad. His arrest remains a high priority of law enforcement and is currently the subject of a reward of up to $10 million through the U.S. Department of State’s Transnational Organized Crime Rewards Program.
In June 2023, Russian national Ruslan Magomedovich Astamirov was charged with a criminal complaint in the District of New Jersey for his involvement in the LockBit ransomware conspiracy and deployment of LockBit ransomware in Japan, France, Florida, and Kenya.
Astamirov remains in custody in the United States and is currently awaiting trial. In addition, two alleged members of the LockBit ransomware gang were arrested in Poland and Ukraine. The arrests were at the request of French judicial authorities.
The US Attorney Philip R. Sellinger further warned that the disruption of LockBit wouldn’t be the last. Investigators will continue to identify and charge all of LockBit’s members. He assured the public that there would be a “spotlight on them as wanted criminals and they will no longer hide in the shadows.”
Monday’s takedown of LockBit’s leak site is the latest action taken by law enforcement agencies in the fight against ransomware gangs. Chainalysis estimates that cybercriminals extorted $1.1 billion in ransom payments in 2023.

