As the Tor Network has developed over the years, it’s always had stability issues. This comes from the very purpose for which Tor was built. It’s completely community-run. This makes it hard to counter DDoS attacks on the network. However, there are ways to figure this out. If Tor users were to set up more guards, we could counter the massive DDoS attacks against onion services.
Key Insights
- Dread admin “Paris” reports instability in the Tor Browser network due to DDoS attacks.
- The Tor network has experienced a rise in DDoS attacks, causing significant downtime.
- Thousands of dark web vendors rely on Dread for information.
- Chief administrator HugBunter cited a persistent adversary targeting the forum to extort dark web markets.
- Moderator Paris expressed concerns over the increased unstable connections to the Tor network. Noting a gradual increase in download times and a substantial rise in Onion service traffic.
- Tor, short for “The Onion Router,” is used for anonymous internet browsing with over 7,000 volunteer-operated relays.
- DDoS attacks target the browser’s onion servers, causing denial of service to normal traffic.
Since its inception in 2018, the Tor Browser has experienced a wave of distributed denial-of-service (DDoS) leaving it virtually unstable at times. Thousands of dark web users rely on the volunteers who make the cogs work and turn the browser into an OpSec safe haven. Recently, the DDoS attacks against websites like the Dread forum have increased significantly.
On May 17th, 2024, Paris, one of Dread’s moderators, aired his concerns about the “consistent uptink in the amount of unstable connections to the Tor network caused by an ongoing DDoS attack on the network, specifically targeting onion services.”
it’s something that’s been echoed in the past. Chief Dread admin, HugBunter has in the past expressed the view that the downtime experienced on the forum was due to a “persistent adversary targeting its hidden services to extort dark web markets that use Dread to communicate with their users.”
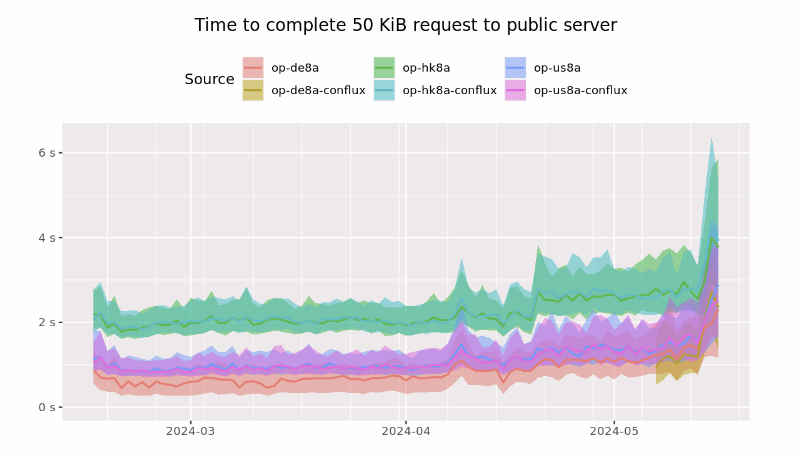
In his post on Dread, the moderator highlighted the gradual increase in time when downloading static files of different sizes over Tor, either from a server on the public internet or from an Onion server.
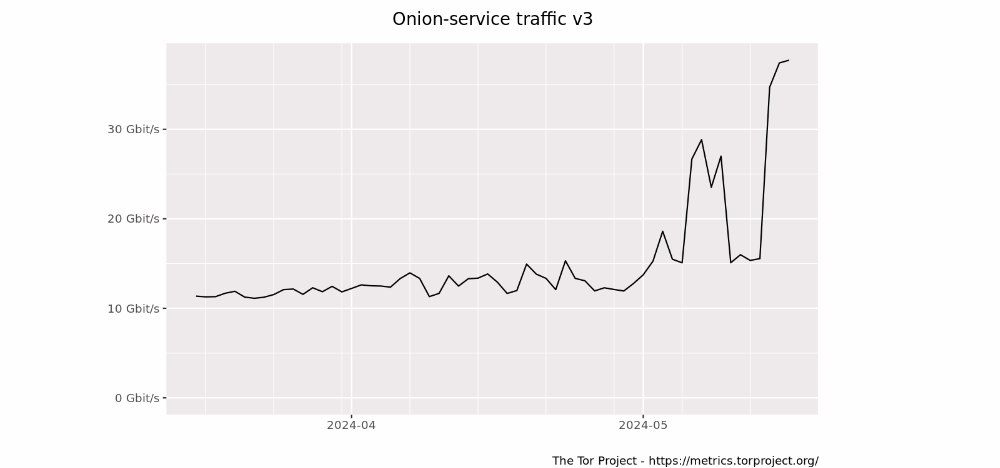
Paris also noted the substantial rise in Onion service traffic of the last month. Furthermore, he said that he would assume that the increase in DDoS attacks wasn’t only on Dread but on some dark web markets.
This was confirmed by Hourglass who claimed “markets like Archetyp or Torzon are also experiencing instability.” He went on to explain that “[He] runs some TOR nodes, I think people don’t actually realize how important they are for the network. They’re the fucking foundations of our whole existence here.”
Paris went on to encourage others to set up a Node themselves
While you might feel powerless against these attacks I do want to remind people that the Tor network is run by a massive amount of volunteers. People who choose to share their processing and bandwidth to the network. Every single server on the network is so important. If you want these attacks to not have as large of an effect on the tor network consider running a tor guard⚠️. Details for how to setup a guard can be found here: https://community.torproject.org/relay/setup/⚠️. If you would rather just donate to have others run a guard on your behalf you can do that at: https://emeraldonion.org/⚠️ or https://nos-oignons.net/⚠️. There are others you can donate to at: https://torservers.net/partners/⚠️.
u/Paris on Dread’s Forum
How DDoS Attacks Affect Tor Network
Distributed denial-of-service attacks have plagued the Tor Browser network in recent months. As a result, dark web markets and discussion forums have experienced a series of downtime rendering them inaccessible to users.
The volunteer-operated relays allow users to have their internet traffic rerouted. A guard relay, or guard node, is a crucial component of the Tor network. It serves as the first hop in a Tor circuit. When a user connects to the Tor network, their connection first goes through a guard relay. This node can see the user’s real IP address, but it only knows the next hop in the circuit, not the final destination or the complete path. This setup helps enhance security and anonymity by limiting the exposure of the user’s IP address to only a few nodes within the network.
By increasing the number of guard relays, the network can better withstand and mitigate the impact of DDoS attacks. As the Tor browser increases in popularity, the need for more onion nodes is becoming evident. Currently, the Tor network is run by over 7,000 volunteer-operated nodes who share their processing and bandwidth with the network.
More relays spread the traffic, making it harder for attackers to overwhelm the network. It also provides backup options, ensuring continued operation even if some are attacked. Additionally, a larger pool of relays makes it harder to trace users and reduces surveillance risks. More nodes allow for better monitoring and quicker responses to attacks.
Essentially, if we can increase guard nodes, a decentralized network with many relays is less vulnerable to targeted attacks. Combating an ever-pressing issue of DDoS attacks on the Tor network will require a team effort from all the volunteer-operated nodes. According to Paris, Dread runs several of its relays on the Tor network and employs TorGuards. In addition, he encouraged other admins who operated on the service to do their part by running layers of TorGuards.
How You Can Set A Guard Relay Up Yourself
To set up a guard relay and strengthen the Tor network:
- Requirements
- Handle 7000 concurrent connections.
- Minimum 10 Mbit/s bandwidth.
- Contribute at least 100 GB of monthly traffic.
- At least 512 MB RAM (1 GB for faster relays).
- Stable IPv4 address.
- At least 200 MB disk space.
- Uptime of more than 2 hours a day (24/7 ideal).
- Software
- Setting up a Relay depends on your OS, see list of options here: https://community.torproject.org/relay/setup/guard/
- Download and install Tor from the official website.
- Configure Tor
- According to website details
- Network Settings
- Open necessary ports in the firewall.
- Set up port forwarding on the router.
- Register and Monitor
- The relay registers automatically.
- Use Nyx to monitor performance and status.

